This website uses cookies so that we can provide you with the best user experience possible. Cookie information is stored in your browser and performs functions such as recognising you when you return to our website and helping our team to understand which sections of the website you find most interesting and useful.
Reference
More than 30 IDM realisations in the Czech Republic and abroad
Consolidation of IdM & AIM
Česká pošta
As part of the IdM & AIM Consolidation project, we addressed several areas and goals, including: managing permissions from a single location; improving security by centrally deploying a strong password policy; overall optimization of access and identities, and more.
Project goal
The IdM & AIM consolidation project in the Czech Post environment would be divided into several areas, each pursuing its own objectives, as follows:
- Managing permissions from a single location
- Improving security by centrally deploying a strong password policy
- Key infrastructure components will be connected to the enVision security system
- Overall optimization of access and identities
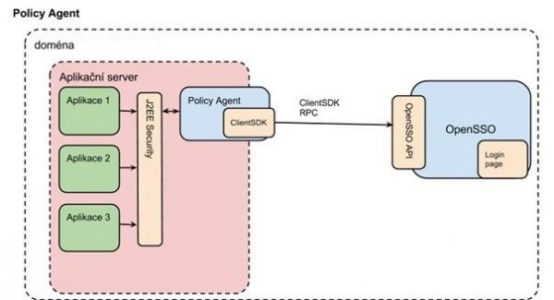
- Development of OpenSSO
Project description
The project was planned for the first half of 2013, when activities fulfilling the initial objectives of the project were to be implemented in parallel. During the implementation, some sub-areas of the project were changed in agreement with the client to better meet his expectations.
In view of the frequent changes and the different demands of the client’s departments, regular status meetings with the client to review the current status and plan the activities for the next fortnight proved very useful, providing an ideal planning horizon with the possibility to react flexibly to changes. Along with this, the team on the contractor side was motivated to try a “scrum like” approach to project delivery, which fitted perfectly into the overall delivery concept.
Solution description
- CRL authentication: the Access manager has been modified to check the validity of certificates and not to allow logins using revoked certificates.
- Password Policy: A password policy was defined for logins to systems connected to IdM. Along with the launch of the new password strength and validity rules, SAP password management applications were added.
- Envision integration: with respect to security, the actions that should be monitored on AIM as part of security monitoring were defined and set up.
- Permissions management: a permissions management methodology was defined and agreed upon, which was then applied to the Czech Post test environment. This entailed setting up approval workflows for assigning permissions to target systems, which must go through a supervisor, the application sponsor and possibly the security department. This included linking the IdM and HPSM tools at the level of forwarding requests for assignment/removal of permissions, with HPSM serving as the registration tool and IdM as the executive tool.
- Restrictions on reserved login names were set to reduce risk and increase security.
- Customization of OpenSSO login page.
- SAML setup on OpenSSO: Setting up the transfer of indents between two client domains.
- Certificate Authentication: Analysis and creation of a sample application for the ability to log in with an X509 certificate.
