This website uses cookies so that we can provide you with the best user experience possible. Cookie information is stored in your browser and performs functions such as recognising you when you return to our website and helping our team to understand which sections of the website you find most interesting and useful.
Reference
More than 30 IDM realisations in the Czech Republic and abroad
Implementation of central identity and role management
Raiffeisenbank
Implementation of central identity and role management in Raiffeisenbank. Six types of systems were connected to CA IdentityMinder (12.5), and more than 3,000 accounts and dozens of roles were managed.
Project goal
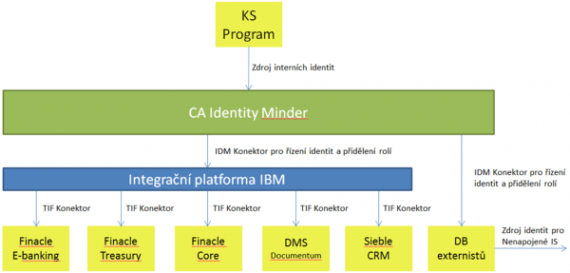
The main objective of the Identity Management integration project at Raifeissenbank (hereinafter referred to as RB) was to ensure unified and centralized management of user accounts and roles for the information systems (hereinafter referred to as IS) that were newly implemented as part of the transformation of the Finacle banking system – E-Banking RM, E-banking Admins, Treasury, Core, DMS Documentum, and CRM Oracle Siebel. Furthermore, to create a platform for role management in existing applications. To connect these systems, it was necessary to connect the authoritative identity source HR system KS Program and to solve the management of external employees who are not registered in HR systems.
Thus, to automatically manage accounts on these systems both in terms of their existence and in terms of roles and permissions. Set up a proper role policy and report any discrepancies.
This objective had to be met not only technically but also procedurally. Therefore, a detailed document describing all processes of the user identity life cycle and the permissions life cycle in the IS was produced. This entire process diagram was developed within the current RB processes. The technical objective was fulfilled by implementing CA IdentityMinder 12.5 (hereafter IDM) and connecting the required IS via the developed connectors.
Another objective of the project was to provide role management lifecycle on individual IS. Its analytical part, dedicated to role design, was handled by CA Governance Minder 12.5. Its process part, dedicated to role approval, role usage, and role assignment, was handled by custom development into the IDM product.
The final goal was to ensure that the proposed procedural and technical solution was generic and robust enough to be used for other RB ISs and subsequently connected to other ISs such as Microsoft Active Directory, Lotus Notes, Oracle DB, and other internal ISs.
Project description
The project was implemented and managed by specialists of AMI Praha a.s. The RAC partner delivered the process analysis and final process design for the identity and role lifecycle. Gordic and freelancer Michal Opatřil contributed to the development of some functionalities.
Benefits for the customer
- Automated actions and controls to increase security
- Unified process for managing user accounts and assigning their roles
- Auditability of changes and requests
- Unified role management process
- Simplification of work for users, approvers and IS administrators
- Uniform user data across all systems
Solution description
After a thorough analysis, a centralized solution and implementation of an IDM was proposed that retrieves data from the KS Program authoritative system (via the IDM Java connector interface) and propagates (or processes and propagates) it to other connected systems. Custom Java connectors were used to connect the systems, where all functionalities were completely programmed (DB externalities, KS Program) and an extra TIF connector for the Message broker (integration platform) for the systems connected via the integration platform (Finacle Core, Finacle E-banking Admins, Finacle E-banking RM, Finacle Treasury, Siebel CRM, DMS).
IDM creates a single database of all employee identities with a single set of attributes associated with them. These accounts are then paired to and managed by the accounts on each endpoint system. The creation, update, and termination of user accounts on individual end systems is thus secured from a single application (IDM) and through a single management process. This process is characterized by various approval workflows, which are defined in the IDM by automatic role assignment rules and attribute values that are constantly enforced or reported on. All processes are then audited and reportable.
At the customer’s request, role lifecycle functionality, role design/expiration/update, approval, creation of rules for role assignment, and import into IDM were implemented into IDM. Roles are thus managed directly in the IDM application. Roles that are tied to the organizational structure are used, aggregating certain permissions and attribute values in the IS that belong to a given job. These roles are assigned either by automatically defined rules (usually according to the assignment to the organizational structure) or by user request in the IDM. A role attribute may have a time limitation and may also carry a requirement to train the worker. A mandatory part of the role definition is the specification of the approval workflow, the training requirement flag, and the automatic assignment rule. The process of assigning a role is conditional on its approval, according to a workflow at several levels (e.g., supervisor, system administrator, trainer). All approvals are done directly in the IDM application and both role assignment and approval are audited.
The project has also implemented an authoritative source of external staff, which is directly in the IDM. Their existence is again conditional on a request in the IDM and after the approval process in the IDM (e.g. system administrator, physical security, supervisor) the user is established in the IDM and is assigned the mandatory roles for external workers (possibly by request mail, access card, etc.). It is then possible for external staff to request access to the connected IS and to audit and report on their accesses and requests.
Single Sign-On (SSO) has been implemented for access to the IDM – i.e. a system where there is no need to log in to the IDM after logging in to the computer (i.e. the AD domain). The IDM is not implemented in HA mode because the availability requirements are not critical and the connected IS are functional without the IDM.
In the initial phase of the project, KS Program, CRM, and DMS were connected to the IDM. Connection of other applications is progressing with Active Directory and others.
